

Read Time:
5
Minutes
Digital Transformation
January 19, 2026
The Future of Endpoint Security from CEO of Kognos
Rakesh Nair, CEO of Kognos shares his thoughts about the future of Endpoint security, and how enterprises need to ready themselves to handle the ever-increasing volume of Endpoint Detection and Response (EDR) data.
“The growing number of threats, despite having deployed numerous endpoint solutions including Antivirus, Host based Firewalls, Host based IDS, etc. has been frustrating every security conscious enterprise. Purely relying on signature based and file-based scanning technologies are not going to offer much protection for anything other than commodity malware and nuisance-ware. Even if they flag a suspicious entity, there is no deep data to go investigate what transpired. Endpoint Protection Platforms added behavioural capabilities and machine learning approaches to detection but to improve visibility a richer dataset is needed, leading to higher prevalence of Endpoint Detection and Response platforms. Combined with threat intelligence and behavioural detection capabilities, this has been the latest thrust by the security industry to thwart attackers who are becoming more and more sophisticated and as a result more and more stealthy by the day. However, this also led to terabytes of data being collected by organizations putting the burden on their security analysts who still rely on manual investigations to sift through this dataset making it humanly impossible. This combined with the fact that most detection products still have high false positive rates makes it completely untenable for manual investigations at these data volumes.”
EDR in 2020
“The collection of metadata at the level of operating system processes provides the highest fidelity of raw data but results in an enormous amount of data to be sifted through for investigations. To offset the challenge of dealing with these enormous data volumes, the EDRs of 2020 and beyond will have to, above and beyond the current detection and response capabilities, have powerful and intelligent automated investigation capabilities. This is key to allowing
1) Security analysts to be able to understand the pre-investigated stories behind each detected signal/alert in minutes by the system, instead of having to manually investigate them sifting through huge amounts of data in hours, days and sometimes weeks. For instance, typical EDR data collected over a 3-month period for a 1000 machine environment can be in terabytes and if the analyst has to investigate a breach that impacted multiple segments of the network over this dataset, it’s going to take weeks if not months to investigate the full breadth of the attack storyline.
2) Enterprises to get better coverage by investigating more than an average of 5 to 10% of alerts that are flagged by the detection systems.
3) Enabling and augmenting the capabilities of analysts at all skill levels with a deep knowledge base that investigates at machine speed.
The future of Endpoint Security
While EDR companies are working to improve data collection, detection and response capabilities a new wave of startups is looking to add automated investigation capabilities on top of these platforms to provide automated investigations, combination of which solves the requirement of rich data collection with automated investigations making the necessary information available in real-time.“
Summary
“EDR while proving to be very effective endpoint security solutions, is also causing a data volume problem which prevents the analysts from being able to do effective investigations. The only way to overcomes is by building automated investigation capabilities into these EDR platforms. The combination of deep and rich data collection combined with intelligent investigations will become a powerful combination to thwart attacks and breaches going forward.”
– Rakesh Nair, CEO Kognos.
“Rakesh’s claims about the data volume problem in detection and response certainly rings true in our experience, with enterprises looking beyond tooling for data models, templates and accelerators that can reduce the resource intensity on identification of security threats and breaches.” – Andy Jefferies, Ntegra, October 2019
About Kognos – Automated EDR Investigations
Kognos, a Silicon Valley startup founded by information security experts and experienced software developers that have created information security applications that are widely used today teamed up to create industry’s first Automated Investigation platform that can seamlessly integrate with existing EDR solutions via APIs and helps alleviate the data volume problem.
The product also integrates with additional data sources to aid with the investigations and for augmenting the storylines generated by this system. For e.g. In a scenario where a malicious insider logs on to a CFO’s laptop using remote desktop connection and make an unauthorized payment using an application running on the CFO’s laptop, information can come from multiple sources. Majority of the investigations will happen on EDR data; however, the story can be augmented by the financial application logs to give a fuller context and risk profile.
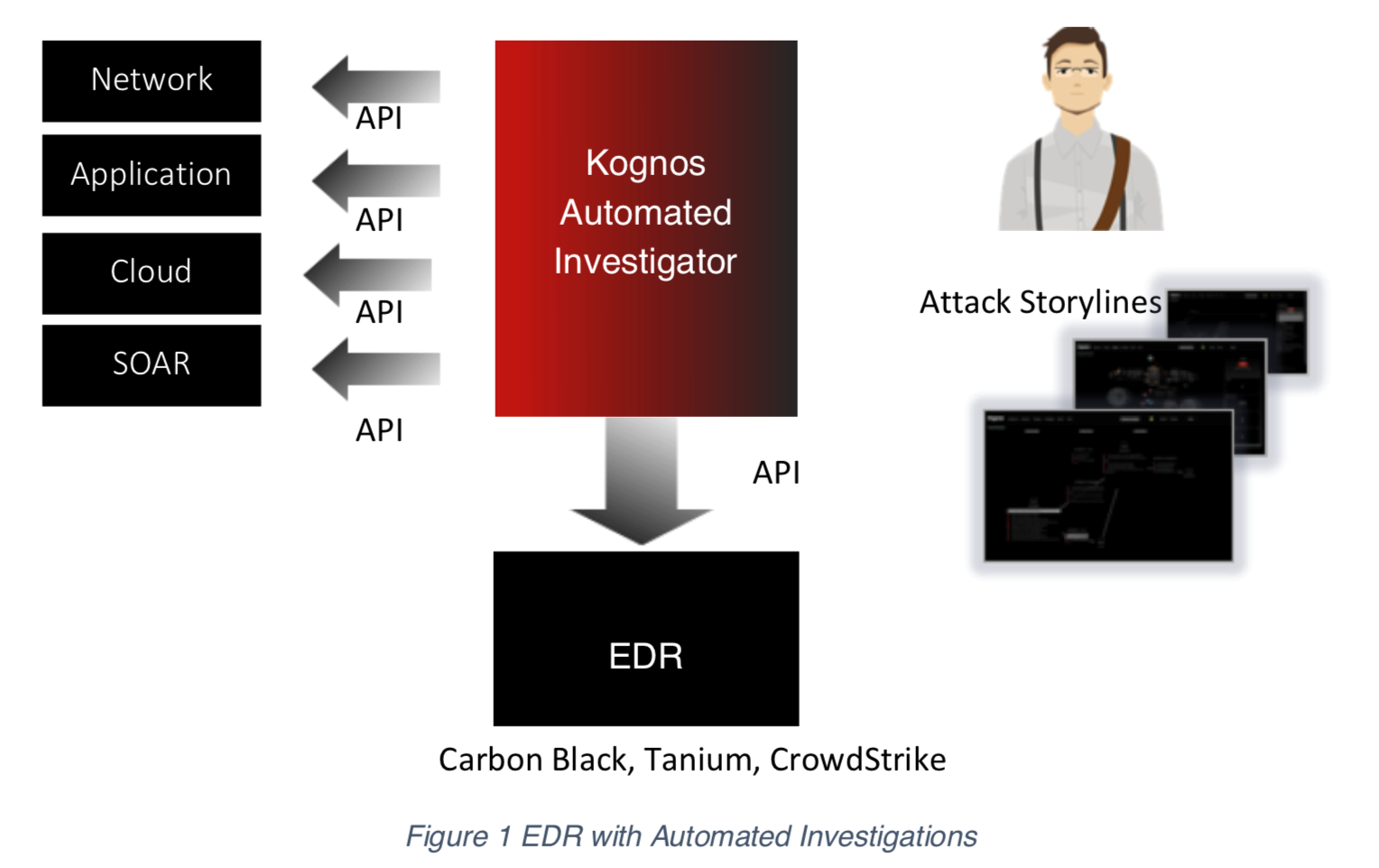
The team has achieved this by building a Knowledge driven AI engine that can ask smart forensic questions similar to those asked by the analysts and is able to collect all relevant evidence from the terabytes of data collected by the EDRs to identify and present evidences to the analyst as incident/attack storylines. The storylines are descriptive providing all the needed context for an analyst to determine what’s happening as well as easily ascertaining the risk associated with a storyline.
Given below is a scenario where an employee clicks on a phishing link and ends up compromising multiple machines in the enterprise.
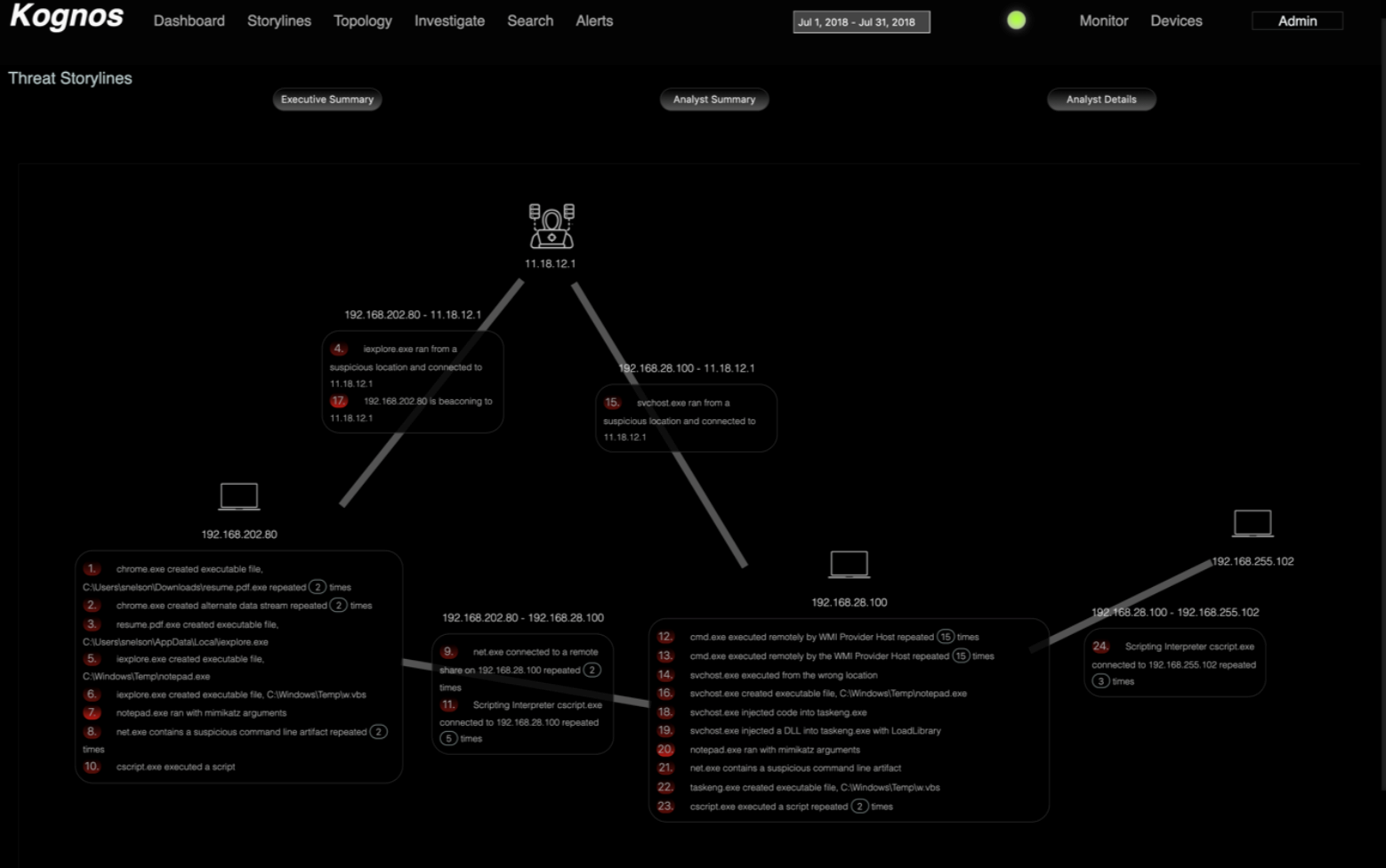
The system automatically traces the path the attacker took throughout the network. We can see the download, execution and entrenchment for the initial foothold in events one through six. Credential Access by mimikatz and lateral movement with w.vbs which is the WMI Remote Command Executor script in events seven through thirteen. Events fourteen through twenty-three show additional malware entrenchment and some Defense Evasion by DLL injection and the attacker moves on to another machine in much the same manor.
To find out more follow this link: https://hubs.ly/H0pnMBJ0
If this resonated, explore Ntegra’s Knowledge Hub for deeper strategy insights, market trends and pragmatic thought leadership.
Ntegra’s Top 3 Legacy System Modernisation Strategies
Ntegra talks to the founder of Device42
How to Continue Delivering Projects in a Post IR35 World
CIO Disruptive Technology Radar
Ntegra Gets Connected at Northumbrian Waters’ Innovation Festival
Judith Halkerston Recognised in New Years Honours List 2021
Ntegra Secures Partnership With Northumbrian Water
4 Ways a SharePoint Intranet Can Be Used to Improve Collaboration and Internal Communication

